
30 May 8 Best Practices To Secure Your Android & iOS Mobile App in 2023
8 Best Practices To Secure Your Android & iOS Mobile App in 2023

Table of Contents
Smartphone technology has revolutionized the way people communicate and interact with the world. Today, a mobile app has become a critical link between companies and their customers. However, many organizations around the world still need to safeguard their business apps when it comes to mobile app security.
Although there are many complex reasons behind safeguarding mobile apps, statistics show that global cybercrime is an alarming issue, as the damages are expected to cost up to $10.5 trillion annually by 2025. On the other hand, the number of mobile devices is projected to exceed 6 billion units globally by 2023.
We need to prioritize mobile apps’ security to avoid more unethical hacking and data breaches. Hence, the security of mobile apps is more important than ever.
What is Mobile App Security?
In essence, mobile app security is a series of efforts performed by mobile app developers to ensure the app is secure from malicious attacks, such as data breaches that give the hacker access to sensitive information.
A holistic security plan entails the measures used to ensure safety during the creation and design of applications and the processes and methods used to keep them safe once they’ve been released to the public.
If you are not aware of the severity of ignoring mobile app security, take a look at some recent alarming statistics about mobile app security:
- 82% of Android devices were exposed to at least one of 25 Android operating system vulnerabilities.
- 63% of popular Android mobile apps on Google Play Store contained open-source components with known security vulnerabilities
- Mobile security flaws in IoS and Android apps are present in 91% and 95%, respectively.
Best Practices to Secure Your Mobile App
With this in mind, here are the top 8 best practices to secure your Android and iOS mobile app in 2023.
Conduct Mobile Application Security Testing
Many people do not have a routine of monthly checkups because they don’t feel sick. However, the issue is not the same when testing your mobile app.
With cybersecurity threats rising, you need comprehensive mobile app security testing to assess your app and identify vulnerabilities. Here are some of the key elements that you should include in your security testing:
- Using the application and learning how it stores, receives and transmits data.
- Decrypting application parts that have been encrypted.
- The application is decompiled, and the resulting code is analyzed.
- Static analysis is used to identify security flaws in decompiled code.
- Using reverse engineering and static analysis knowledge to drive dynamic analysis and penetration testing.
- Using dynamic analysis and penetration testing to assess the effectiveness of the application’s security controls (e.g., authentication and authorization controls).
Add Code Obfuscation
As mobile apps can be reverse-engineered with freely available disassemblers or decompilers, hackers can readily exploit sensitive information from the app or add malicious code to your app. One effective way to prevent this is using code obfuscation. It makes it challenging for hackers to access and study your applications’ source code.
Code obfuscation is a security strategy for making the code difficult to understand by changing an executable code without affecting its function so that it is inaccessible to hackers. By making it difficult to reverse engineer a mobile app, developers protect the intellectual property of their products against security risks, unwanted access, and the discovery of application flaws.
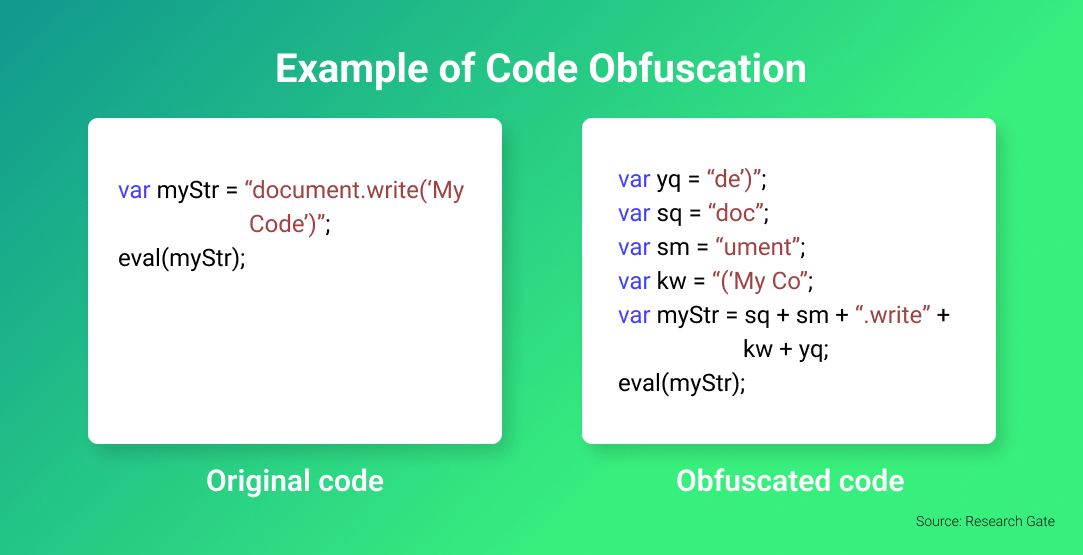 Usually, developers combine various techniques to create a layered effect. Some techniques you can use to harden your iOS and Android code include:
Usually, developers combine various techniques to create a layered effect. Some techniques you can use to harden your iOS and Android code include:
- Name obfuscation: Alter the name and variables of the code
- Control flow obfuscation: Change the code’s logical structure to make it less predictable and traceable
- Ordering obfuscation: Rearrange and alter the structure of the source code
- String encryption: conceals the strings in the executable using encryption and only recovers the values when necessary to run the program.
- Dummy code insertion: Adding dummy code to the program to make it harder to read and reverse engineer without affecting the program logic and outcome
Encrypt Your Data in Transit
Data in transit refers to information sent from one source to another. In contrast with data at rest, data in transit is active and can be transported to different locations within or between computer systems via cables and wireless transmission. This data can flow over a network and be read, updated, or processed.
One example of data in transit is when data from a mobile app is transferred from local to cloud storage. If you want to keep your iOS app’s data safe while it’s being sent, encrypt it and keep attackers from getting to it.
Encrypting the data in transit is the best way to keep it safe. Any network communication that requires authentication or involves material that is not publicly available, such as emails, should be required to encrypt data in transit. End-to-end encryption can protect user data whether they communicate via email, SMS, or chat platforms.
To do this, you’ll need to integrate an encryption service into your app. There are two ways to encrypt your data in transit: symmetric encryption with a predetermined session key or a certificate and asymmetric encryption for securely exchanging session keys.
Another great way to encrypt data in transit is using cryptographic protocols such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS), which authenticate data transit between servers or systems and offer endpoint encryption solutions that prevent unwanted access.
Implement High-Level, Multi-Factor Authentication
According to Kaspersky, stolen or weak credentials are one of the reasons for data breaches. Therefore, developers should implement multi-factor authentication in their apps.
For instance, the app with login details should only accept strong alphanumeric passwords. A strong password should be 10 characters long, contain upper and lower-case letters, numbers, and symbols, and be unique for each account.
However, more than single-factor authentication is needed to ensure your app’s security. To further secure your app, consider combining Single Sign-On (SSO) or enterprise password authentication with multi-factor authentication (MFA).
By using SSO, passwords are either replaced by secure tokens using protocols such as SAML, or strong credentials are generated for users and entered automatically into login forms. This reduces the burden of constantly asking users for password changes and removes human limitations in creating secure passwords.

When combined with MFA, you are providing an added level of security by requiring more than one form of identification to log into an account or access sensitive data. For sensitive apps like banking and insurance apps, biometrics such as fingerprint recognition or a retina scan with multi-factor authentication are highly encouraged.
Prevent Binary Planting & Malicious Code Injection
Attackers like to use dynamic and static code injection techniques to inject malicious code into an app and get that code executed by the app or the server. Once the injection is successful, it can lead to data loss and security breaches. Therefore, taking care of malicious attacks and binary planting is essential if you aim to secure your Android and iOS apps.
While use cases differ for different conditions, whitelisting for input validation and encoding HTML outputs are two best practices to eliminate code injections. Whitelisting provides security teams with stricter control over what data or types of input the application can process and thus reduces the likelihood of an attacker executing malicious code. Encoding HTML outputs converts malicious input into safer representations where user data can be displayed but not executed as code.
If you want to secure your app further, you may also apply additional techniques, such as tamper detection technologies, protected third-party libraries, improved session handling, RASP security, and secured backend and API connections.
Using FCM instead of SMS
SMS was used to push data from servers to apps when Firebase Cloud Messaging (FCM, formerly known as Google Cloud Messaging (GCM), did not exist, but GCM is now widely used. However, if you have not yet switched from SMS to GCM, you should.
This is because the SMS protocol is not secure or encrypted. SMS can also be accessed and read by any other app on the user’s device. GCM communications are authenticated on the client side by registration tokens that are reset regularly and on the server side by a unique API key.
However, there are a few cons with GCM, such as scaling limits and a lack of support for non-Google platforms. If you are concerned about using GCM or have more budget, consider other messaging alternatives such as AWS SNS, Airship, OneSignal, Azure Notification Hubs, etc.
Implement the Latest Data Encryption Techniques
As mobile app developers, we know that data encryption is necessary. However, even the most popular cryptography algorithms, such as MD5 and SHA1, are frequently inadequate to meet the ever-increasing security demands.
Therefore, it is crucial to stay current with the most recent security algorithm and employ modern encryption techniques such as AES with 512-bit encryption, 256-bit encryption, and SHA-256 for hashing.
In addition, you should combine cryptography with penetration testing and threat modeling on your mobile applications before they go live to ensure absolute security.
Besides, it’s important to keep track of the latest Android and iOS security patches to update your app and avoid exploiting known vulnerabilities.
Utilize the Latest Security Patches
Security patches are crucial because they help patch security gaps, eliminate outdated features, and install new ones. Software updates typically repair security gaps and give software patches to thwart hacker assaults.
New security patches are released for both Android and iOS regularly. Therefore, incorporating the latest security patches into the codebase keeps your app up to date and protects your users from malicious attacks.
Key Takeaways
These days, where cyber threats are no joke, you should take all opportunities to ensure your mobile app is safe and secure. These top 8 best practices will help you protect your users’ data and secure their experience with your app. Although implementing these best practices can be overwhelming or time-consuming, it can make a difference in your app’s functionality and usability.
When it comes to mobile app security, you should remember to:
- Check and monitor your mobile app security regularly, as today’s cybersecurity landscape is changing at a dizzying pace.
- Combine multiple security techniques and practices as mentioned above to maximize the security of your iOS or Android mobile apps.
- Keep yourself updated with the latest mobile app security news, trends, and techniques.
Having an app that follows best practices can help you retain users, gain new ones, and reduce your risk of experiencing data breaches. With these best practices in place, you can rest easy knowing that your app is secure, and your users can rest easy knowing their data is safe.





No Comments