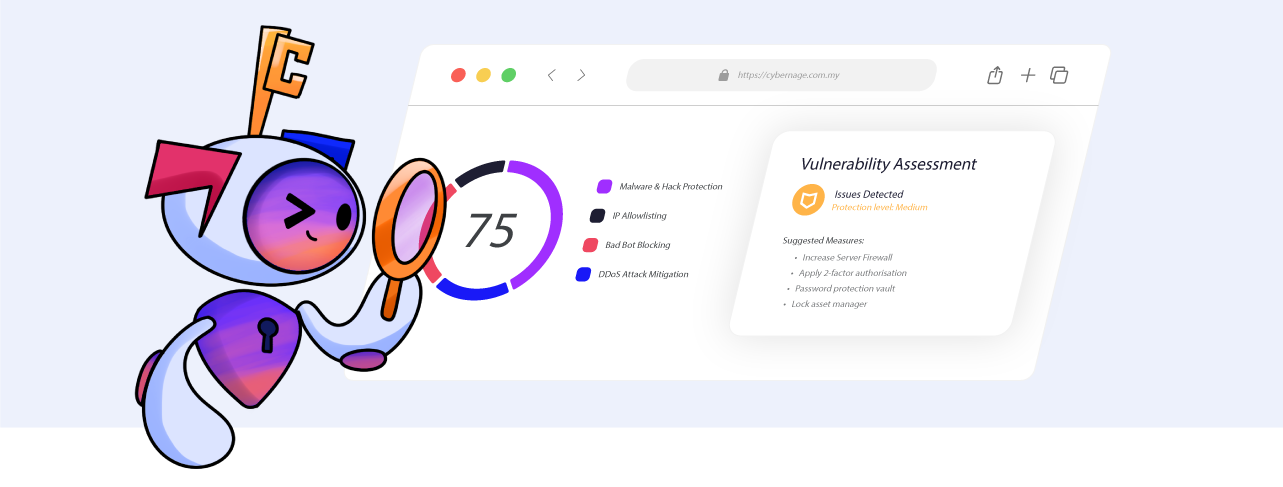
Vulnerability Assessment
Connect with our experts to probe your web applications for vulnerabilities and provide actionable solutions to keep hackers at bay.
Protect your business from cyber threats with our comprehensive vulnerability assessment services. Our team of experts uses the latest tools and techniques to identify vulnerabilities in your network and applications and provide recommendations for remediation
Why wait for a cyber disaster to strike? Take charge of your security destiny by proactively identifying and addressing vulnerabilities lurking within your systems.
The stakes are high in the cybersecurity game, and the cost of a breach goes beyond financial losses. It’s time to mitigate risks and protect what truly matters. Start identifying and neutralising vulnerabilities before they turn into costly breaches.
In an interconnected business world, your security is only as strong as your weakest link. Ensure your vendors and partners meet your security standards with vulnerability assessments.
When it comes to security audits and assessments, preparation is key. Stand tall and showcase your commitment to robust security controls with vulnerability assessments.
Gain a competitive edge in cybersecurity by harnessing our advanced threat intelligence. We identify emerging threats and provide real-time insights into vulnerabilities specific to your industry. Stay one step ahead of cybercriminals with proactive mitigation strategies tailored to your unique needs.
Take control of your security with our comprehensive scanning and analysis. Using cutting-edge vulnerability assessment tools and techniques, we provide a detailed view of your security posture. Uncover hidden vulnerabilities and understand the precise steps needed to fortify your defenses.
Don’t settle for just vulnerability identification—partner with our experienced cybersecurity professionals for expert guidance and remediation. We help you navigate the assessment results, prioritising vulnerabilities based on their potential impact. With our guidance, you can address the most critical risks and achieve a robust security framework.
We don’t stop at a one-time assessment; we stay vigilant and monitor your systems 24/7. Our proactive approach alerts you to new vulnerabilities and provides timely recommendations for remediation, ensuring uninterrupted protection for your digital assets.
Safeguard your network infrastructure with a comprehensive evaluation that uncovers vulnerabilities, empowering you to fortify your defenses and protect against potential cyber threats. Gain peace of mind knowing your network is secure.
Bolster your web application security through a meticulous assessment that identifies vulnerabilities and strengthens your defenses. Safeguard customer data, maintain trust, and stay ahead of evolving cyber risks.
Enhance your wireless network security with a tailored evaluation that exposes weaknesses and provides actionable insights. Strengthen access controls, protect sensitive information, and maintain a resilient wireless environment.
Ensure the security of your cloud systems and data through a thorough assessment that uncovers vulnerabilities and ensures compliance. Protect your digital assets, maintain data integrity, and establish a robust cloud security framework.
Safeguard your premises and assets with a comprehensive evaluation of your physical security measures. Identify vulnerabilities, strengthen access controls, and create a secure working environment for your organization.
Enhance your employees' defense against social engineering attacks through simulated assessments and targeted training. Strengthen awareness, reduce human error risks, and create a resilient security culture.
Safeguard your network infrastructure with a comprehensive evaluation that uncovers vulnerabilities, empowering you to fortify your defenses and protect against potential cyber threats. Gain peace of mind knowing your network is secure.
Bolster your web application security through a meticulous assessment that identifies vulnerabilities and strengthens your defenses. Safeguard customer data, maintain trust, and stay ahead of evolving cyber risks.
Enhance your wireless network security with a tailored evaluation that exposes weaknesses and provides actionable insights. Strengthen access controls, protect sensitive information, and maintain a resilient wireless environment.
Ensure the security of your cloud systems and data through a thorough assessment that uncovers vulnerabilities and ensures compliance. Protect your digital assets, maintain data integrity, and establish a robust cloud security framework.
Safeguard your premises and assets with a comprehensive evaluation of your physical security measures. Identify vulnerabilities, strengthen access controls, and create a secure working environment for your organization.
Enhance your employees’ defense against social engineering attacks through simulated assessments and targeted training. Strengthen awareness, reduce human error risks, and create a resilient security culture.




Vulnerability assessment is a proactive cybersecurity measure that identifies weaknesses in your systems, ensuring they are secure against potential threats. It helps safeguard your sensitive data, maintain compliance with cybersecurity regulations, and protect your business from cyber-attacks.
Regular vulnerability assessments are crucial to maintaining a strong security posture. The frequency depends on various factors such as industry regulations, system complexity, and evolving threats.
Generally, conducting vulnerability assessments at least annually or whenever significant changes occur in your infrastructure or applications is recommended.
Vulnerability assessment can uncover various vulnerabilities, including software vulnerabilities, configuration weaknesses, outdated patches, insecure network architecture, etc. By detecting these vulnerabilities, you can address them promptly, mitigating the risk of data breaches and other cyber threats.
Vulnerability assessment plays a crucial role in meeting regulatory compliance requirements. It helps you identify vulnerabilities potentially exposing sensitive data and violating industry-specific regulations.
Our vulnerability assessment services in Malaysia can help you to demonstrate a proactive approach to security and protect your organisation from compliance-related penalties.
While a vulnerability assessment alone cannot guarantee prevention of all cyber attacks, it significantly reduces the risk by identifying and addressing vulnerabilities before they can be exploited.
By proactively securing your systems and implementing recommended remediation measures, you strengthen your defenses and deter potential attackers.
Our vulnerability assessment solutions in Malaysia empower you to stay one step ahead of cyber threats, minimizing the likelihood of successful attacks.
Absolutely! Vulnerability assessment is essential for businesses of all sizes, including small businesses. In fact, small businesses are often targeted by cybercriminals due to their perceived vulnerabilities.
Conducting regular vulnerability assessments tailored to your business size and needs helps you identify and address potential weaknesses, protect sensitive customer information, and maintain your reputation.
It typically provides a comprehensive report outlining identified vulnerabilities, their severity levels, and recommended remediation measures. The report includes actionable insights, prioritised recommendations, and a roadmap to enhance your security posture.
While it’s possible to perform vulnerability assessment on your own by using a cybersecurity tool, it’s recommended to engage a professional cybersecurity provider as they provide a higher level of accuracy and help prioritise remediation efforts effectively.
While automated tools like Astra security can identify known vulnerabilities, cybersecurity experts possess the ability to leverage their human intelligence to uncover hidden vulnerabilities that automated tools may overlook.
Cybersecurity experts can also provide vulnerability assessments tailored to your unique business needs and industry-specific risks. Hence, the assessment is more targeted and relevant to your specific security challenges, resulting in a more effective and actionable assessment report.
Contact Cybernage as your trusted cybersecurity partner in Malaysia to ensure a thorough assessment.
It depends on the size and complexity of your systems and the scope of the assessment. It can range from a few days to several weeks.
However, we always optimize the assessment process to deliver efficient and timely results without compromising quality.
Our experienced team will work closely with you to establish a suitable timeline based on your specific requirements, ensuring minimal disruption to your business operations.
We stand out due to our deep expertise, comprehensive approach, and commitment to exceeding expectations.
As one of the reliable cybersecurity providers in Malaysia, we combine advanced scanning techniques, industry-leading tools, and tailored methodologies to identify vulnerabilities specific to your organisation.
Our detailed reports, actionable insights, and expert recommendations empower you to make informed decisions and enhance your security posture effectively.
Worried of data breaches or malicious attacks happ
Are you worried about data breaches? Check out thi
R00TK1T cyberattacks have targeted multiple local
Please note that the person filling this information collection form must possess minimum IT knowledge or act as a cybersecurity personnel from your company. This is to ensure that the information provided is accurate towards your business requirements. Alternatively, we recommend seeking the assistance of a team member with a detailed understanding of the application.
Follow Us