
16 Feb A Complete Timeline of R00TK1T Cyberattacks in Malaysia [Updated]
A Complete Timeline of R00TK1T Cyber Attacks in Malaysia [Updated]

Table of Contents
You’ve probably heard of the infamous R00TK1T hacker group by now. They dotted the news with their claims of hacking governments and notable institutions around the world.
They set their sights on Malaysia in late January 2024, launching an alleged series of cyber attacks on government bodies and local institutions. This includes attacks on the Ministry of Education, the Federal Court of Malaysia, Maxis, and most recently, the Aidan Group.
This cyber attack campaign is currently ongoing, although R00TK1T has since announced Iraq as a new target.
In light of this, we’ve compiled a complete timeline of R00TK1T’s activities in Malaysia. Read on for a comprehensive overview of the persistent cyber attacks launched by this hacker group.
Who or What is R00TK1T?
R00TK1T is an international hacker group which has targeted financial institutions, government databases, and multinational corporations globally. This group is known for their relentless and sophisticated cyberattacks.
Their name originates from the cyber term “rootkit” which is a form of malicious software that allows unauthorised access to a network or system. This allows hackers to steal data and access files without detection.
Prior to Malaysia, R00TK1T was involved in attacks against the digital infrastructure of Lebanon and the corporations: L’Oréal, Qatar Airways, and Sodexo. The cyberattack on Lebanon was confirmed by the Lebanese Social Affairs Ministry, while scepticism surrounds the attacks against the remaining institutions.
On 26th January 2024, the hacker group announced Malaysia as their next target through their Telegram channel: R00TK1T ISC Cyber Team. The group warned that Malaysians will “witness the collapse of their digital infrastructure”.
Security Solutions Provider iZOOlogic stated that the announcement had been posted to the dark web as well. As this hacker group has a track record of successfully infiltrating high-security systems, iZOOlogic believed that the threat must be taken seriously.
On 30th January 2024, R00TK1T revealed that Malaysia was targeted because the country had allegedly provided sanctuary to “those who perpetrate terror and engage in cyber warfare in the Middle East conflict”. Therefore, the group claimed the cyberattacks were an act of justice and vengeance.
A Complete Timeline of R00TK1T Cyberattacks in Malaysia
26 January 2024: R00TK1T announced the launch of a series of cyberattacks in Malaysia. They stated their intent to infiltrate the Malaysian government and local institutions.
30 January 2024: R00TK1T claimed to have infiltrated Aminia, a telecommunications and oil palm plantation in Malaysia. Sources state that the group may have attacked Aminia’s backend system.
Aminia confirmed a breach of their externally hosted services but claimed no sensitive data was leaked.
4 February 2024: R00TK1T claimed to have infiltrated networks of IT companies and the ‘core’ of the Malaysian government.
R00TK1T claimed to have infiltrated the YouTutor courses website in Malaysia. The hacker group claimed that they obtained personal information such as phone numbers, email addresses, physical addresses, and more. This was accompanied by a supposed sample of the mentioned data.
5 February 2024: R00TK1T claimed to have infiltrated Maxis, a local telecommunications company in Malaysia. The hacker group stated their intention of releasing customer data to the public.
R00TK1T demanded Maxis publicly acknowledge the breach into their system. This breach was investigated by Maxis, who stated that it had identified a “suspected incident involving unauthorised access” to one of their third-party vendors, but did not identify anything related to its own systems.
If Maxis refuses to issue a statement, R00TK1T threatened to shut down Maxis’ systems and expose its data every two hours. This was accompanied by an alleged screenshot of the company’s employee dashboard and another alleged screenshot of a vital part of the company’s backend system.
Later, R00TK1T claimed to have infiltrated Maxis Kulim’s network and “plunged their system into the dark ages”. One of the attached screenshots appears to show that the hacker group may have executed a factory reset on one of the telco’s Agrotech-related systems.
The hacker group goes on to give a ‘final warning’ to Maxis. They share a screenshot of a system that appears to show current Internet connections at Quayside Mall in Kota Kemuning, Selangor.
6 February 2024: R00TK1T threatened Maxis again, as the corporation denied any infiltration to their systems.
The group stated their increased determination to carry out the cyberattacks with their alleged team of 52 hackers.
In the same message, the hacker group expressed gratitude to employees who had allegedly provided them with inside information regarding the authorities and large companies in Malaysia.
7 February 2024: R00TK1T announced that they have unleashed a “devastating cyberattack” on Malaysia, sharing a screenshot of what appears to be the information of several local companies.
The group claimed to have infiltrated AMC University College in Malaysia. The hacker group stated that they obtained personal information such as names, addresses and contact details of students and staff members at the college.
Later that day, the hacker group claimed that “thousands of SMS messages” were sent to Maxis customers. They also claimed that “large sums of money” disappeared from the customers’ bank accounts and were transferred to third parties.

8 February 2024: R00TK1T claimed to have infiltrated the Ministry of Education’s system.
The group also claimed to have infiltrated Integrated Network Solutions (INS), a next-generation business-technology solutions company in Malaysia.
9 February 2024: R00TK1T claimed to have infiltrated Raine, Horne & Zaki Property Management Sdn Bhd in Malaysia. The group further claimed that they now possess the usernames and passwords belonging to property managers.
On the same day, R00TK1T announced a temporary cessation of their cyberattacks on the Malaysian government. According to Cyber Express, speculations arose that the cessation was due to backchannel negotiations with the Malaysian government, or a scarcity of resources to continue their cyberattacks on Malaysia.
10 February 2024: R00TK1T announced that the cyberattacks against Malaysia will resume.
The group also threatened Dragonforce, a group of hackers in Malaysia. Dragonforce is a pro-Palestinean group that has notably hacked into Israeli Institutions and multiple Indian websites. R00TK1T threatened to “expose their feeble attempts at hacking” and warned local hackers not to oppose R00TK1T.
Later that day, R00TK1T claimed to have infiltrated the Federal Court of Malaysia. This claim was verified by iZOOlogic researchers.
11 February 2024: R00TK1T claimed to have successfully infiltrated and taken control of multiple websites belonging to the Malaysian government, including Berita RTM. This claim was verified by iZOOlogic researchers.
Later that day, R00TK1T executed a ransom attack on the Aidan Group. The hacker group claimed to have infiltrated Aidan’s systems and gained control over valuable data. The hacker group claimed that Aidan’s extensive customer base “includes large companies and the Malaysian government”.
12 February 2024: R00TK1T launched a full-scale cyberattack against Iraq named ‘Operation Thunderstorm’, leading some sources to believe that the hacker group has ended their campaign against Malaysia.
15 February 2024: R00TK1T demanded that the Aidan Group and the Malaysian government acknowledge the alleged successful infiltration and ransom attack.
16 February 2024: R00TK1T claimed to have successfully infiltrated Malaysia’s Institute of Diplomacy and Foreign Relations. This was accompanied by a file supposedly containing the institute’s user data, revealing private information such as full names, email addresses, and IDs.
17 February 2024: R00TK1T demanded that the government acknowledge the alleged successful cyber attacks. If their demands were not met, the hacker group threatened to attack Malaysia’s electrical infrastructure.
On the same day, they initiated an alleged attack on the charging infrastructure for electric vehicles across Malaysia.
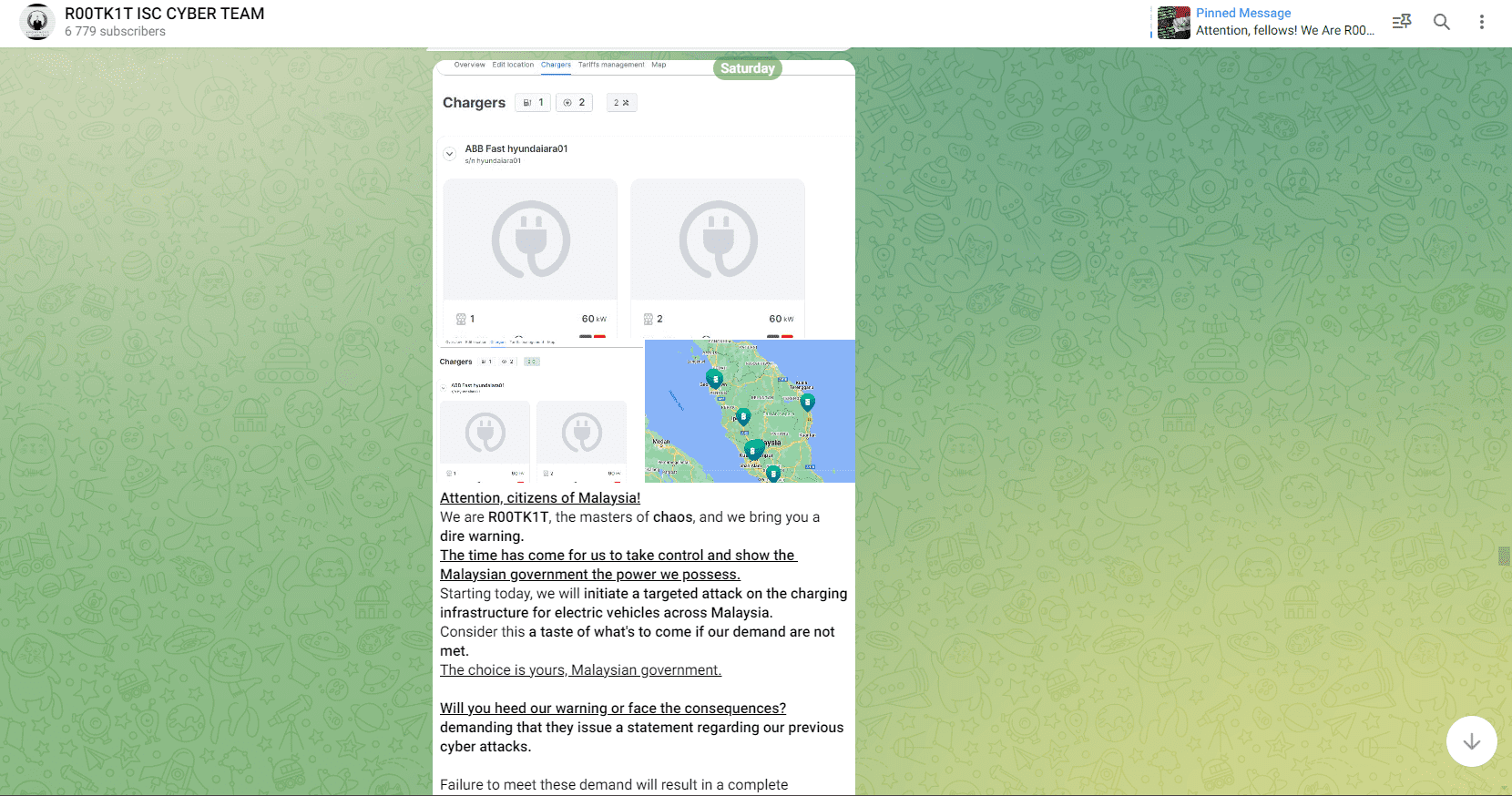
Sources analysed the screenshots shared by the R00TK1T and stated that the hacker group may have access to the GO To-U backend system, TNB Electron and other TNBX chargers. However, GO To-U stated they found no evidence of a security breach.
R00TK1T claimed that the government’s failure to acknowledge the alleged cyberattacks will result in a “complete shutdown of electricity throughout Malaysia”.
18 February 2024: R00TK1T allegedly leaked the database of the smart waste management system in Malaysia.
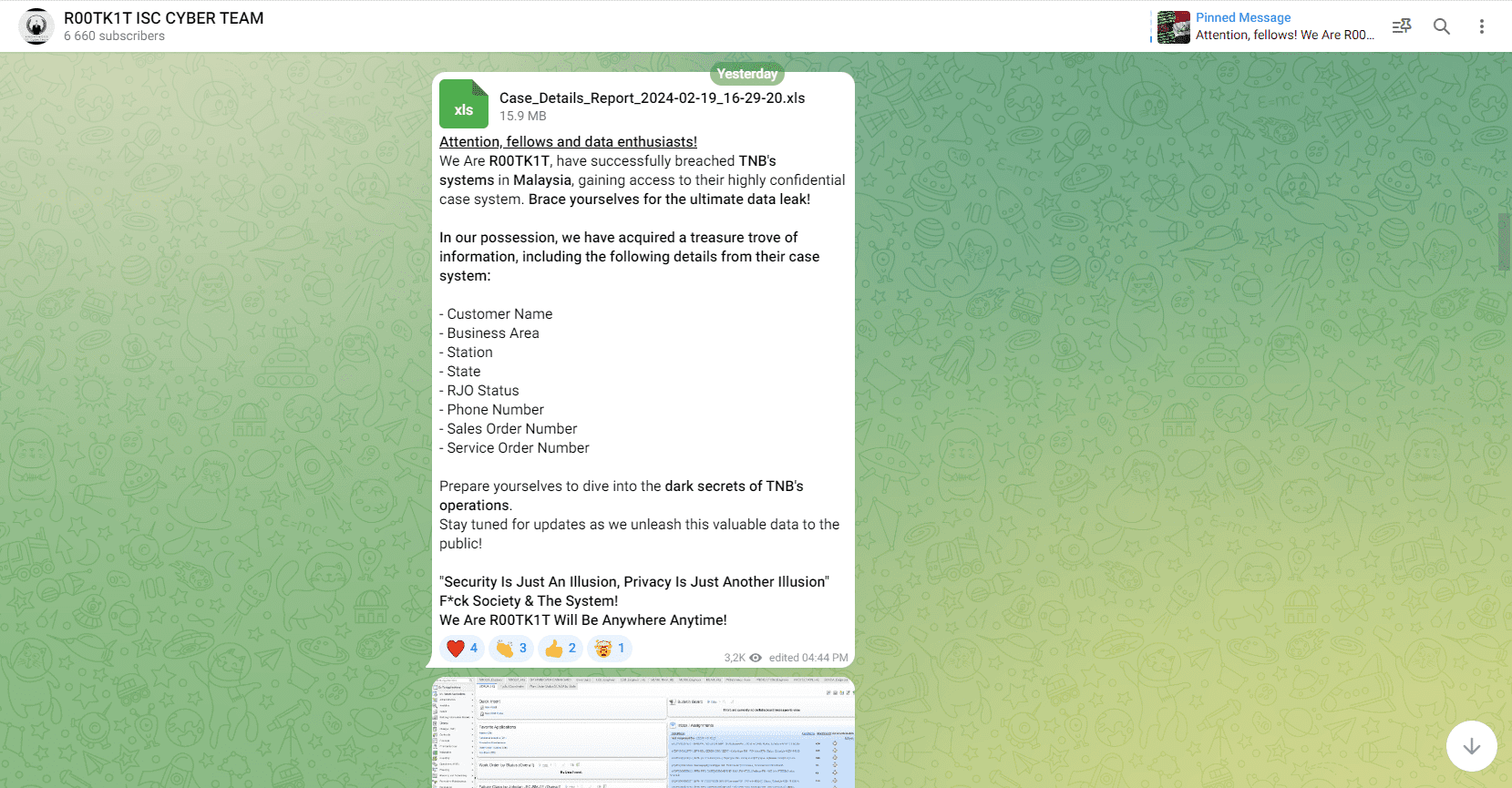
19 February 2024: R00TK1T claimed to have successfully infiltrated Tenaga Nasional Berhad’s (TNB) systems in Malaysia.
The hacker group claimed that they possess details from TNB’s case system such as customer name, business area, station, state, RJO status, and more.
Later, R00TK1T claimed to have successfully infiltrated and stolen 27TB of data from the National Council for Population and Family Development (LPPKN) cloud servers.
They further claimed to have infiltrated the PADU organisation. However, it was later revealed that the ‘PADU’ files shown by R00TK1T belonged to LPPKN’s Management and Service Delivery Unit.
20 February 2024: R00TK1T claimed to have successfully hacked and disabled all government systems in Putrajaya.
They also released the alleged user details of two notable figures associated with Perbadanan Putrajaya, including their email addresses and passwords.
This cyberattack is still ongoing. Do check in from time to time for the latest updates!
Key Takeaways
This timeline illustrates the ever-present danger of cybersecurity attacks. This hacker group allegedly infiltrated the security systems of well-known institutions across Malaysia.
Some of these cyberattacks have been verified, while others have yet to be addressed. Therefore, the general public and organisations are advised to stay updated on cybersecurity news and fortify their security systems.
We should prioritise regular software and system updates, strong password management, and firewall installation. Organisations may employ extra steps such as employee cyber awareness training, third-party security assessments, and incident response planning.
To complement these strategies, consider acquiring regular assessments from cyber security organisations which provide fresh perspectives and help further secure your systems.
In Malaysia, Cybernage stands out as a reliable cybersecurity management company offering a range of services to assess and fortify your systems. Their expertise can provide valuable insights to ensure the continued security of your assets.
Here is a list of Cybernage’s available services:
- Vulnerability Assessments
- Web Application Penetration Testing
- System & Network Penetration Testing
- Red Teaming
- Forensic (Ransomware, Advanced Persistent Threat)
- Server Hardening
FAQ
What are the types of cyberattacks?
Common types of cyberattacks include phishing, malware, ransomware, distributed denial-of-service (DDoS) attacks, man-in-the-middle (MITM) attacks, password attacks, and spoofing.
How do cyberattacks happen?
Cyberattacks happen through various methods such as phishing emails, malware attacks, and ransomware.
Cyberattacks are also divided into untargeted and targeted attacks. Untargeted attacks randomly target as many devices, services or users as possible, while targeted attacks single out a particular organisation.
How can cyberattacks be prevented?
Cyberattacks can be prevented through firewalls, malware protection, patch management, password policy and user access control. We also suggest getting cyber security assessments from relevant organisations to obtain a new perspective and further secure your systems.
How common are cyberattacks?
Cyberattacks are prevalent and occur globally, affecting individuals, businesses, and governments. According to AAG, there is an average of 97 cybercrime victims per hour. This means there could be a victim of cybercrime every 37 seconds.




No Comments