
30 May A Beginner’s Guide to Vulnerability Assessment
A Beginner’s Guide to Vulnerability Assessment

Table of Contents
A Beginner’s Guide to Vulnerability Assessment
Each year, more than 180,000 security vulnerabilities are discovered. It’s no surprise that cybercrime has increased significantly in recent years with so many potential infrastructure weaknesses and system attacks. Vulnerability assessments can serve as a preventative measure against such threats when they are performed correctly and regularly.
What Is Vulnerability Assessment?
A vulnerability assessment identifies, classifies, and prioritizes vulnerabilities in network infrastructure, computer systems, and applications. Having a vulnerability can expose an organization to cyber threats or risks. Often, vulnerability assessments are performed using automated testing tools such as network security scanners.
Regular vulnerability assessments can be extremely beneficial to organizations that are subject to ongoing cyber-attacks. The threat actors are constantly looking for vulnerabilities that can be exploited to breach applications, systems, and perhaps entire networks.
Organizations constantly introduce new components as well as discover new vulnerabilities in existing software and hardware components. By combining vulnerability assessments with vulnerability management programs, security weaknesses can be identified and fixed, and security posture can be improved.
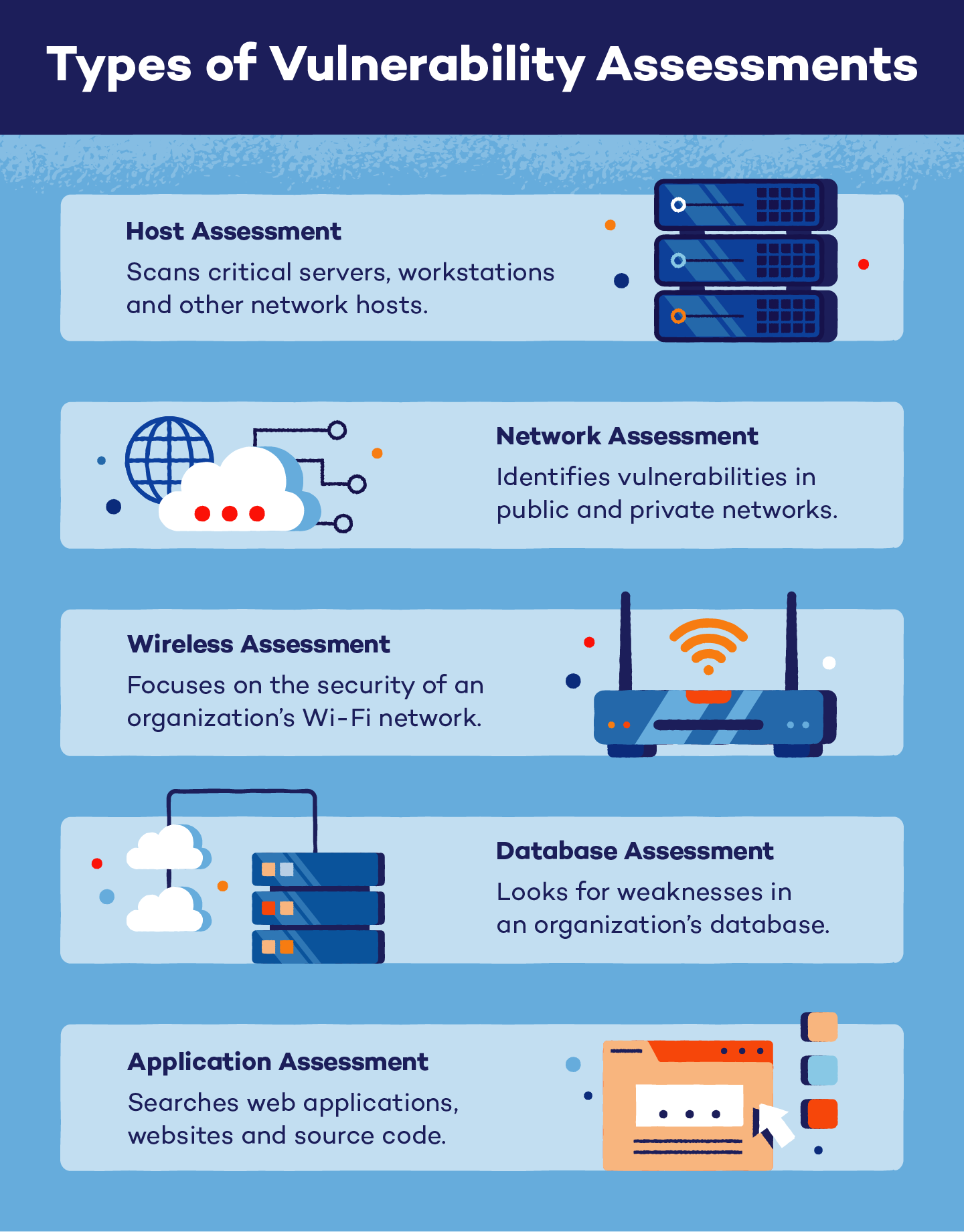
Types of Vulnerability Assessment Tools
Today’s vulnerability assessments are conducted using automated scanning tools. Tools used to scan for vulnerabilities in an environment fall into the following categories:
Network-based scanning
It is used to identify potential security threats to a network. Using this type of scan, vulnerable systems can also be detected on wired or wireless networks.
Host-based scanning
The purpose of this tool is to identify vulnerabilities on servers, workstations, and other network hosts. In this type of scan, vulnerable ports and services are analysed, providing insight into the configuration settings and patch history of the scanned system.
Wireless network scans
This type of scan focus on identifying the security weaknesses in a Wi-Fi network within an organization. By performing these scans, it will be possible to identify malicious access points and ensure that wireless networks are configured securely.
Application scans
It focuses on detecting known software vulnerabilities and misconfigurations on websites and mobile applications.
Database scans
The priority of database scans is to detect vulnerabilities in a database server that may allow database-specific attacks, such as SQL injection and NoSQL injection, as well as general vulnerabilities and misconfigurations.
Why are Vulnerability Assessments Important?
By conducting vulnerability assessments, security teams are able to identify and resolve security threats and risks consistently, comprehensively, and clearly. There are several benefits to an organization from this.
Firstly, it allows early and consistent identification of threats and weaknesses in IT security. In this manner, potential security threats and vulnerabilities are addressed before they may be exploited.
Secondly, remediation actions can be taken to close any gaps and protect sensitive information and systems. Organizations can reduce the risk of data breaches and other unauthorized access by identifying and addressing vulnerabilities.
Lastly, vulnerability assessments are useful in helping organizations maintain compliance with cybersecurity regulations and laws, such as HIPAA and PCI DSS. Organizations can avoid costly fines and damage to their reputation by ensuring their security measures are current and meet regulatory requirements.
Why do I need a Vulnerability Assessment?
A vulnerability assessment provides an organization with information about any security weaknesses in its environment. Additionally, it provides guidance on how to assess the risks associated with those weaknesses.
It is through this process that an organization can gain a better understanding of its assets, security flaws, and overall risk. This reduces the likelihood that a cybercriminal will breach its systems and catch the business by surprise.
Conclusion
Vulnerability assessments are an essential part of ensuring the security of your network. Using them will allow you to mitigate security breaches by identifying which areas of your network need patching and where you should begin. It is recommended that you conduct vulnerability assessments on a quarterly basis and whenever there are changes made to your system.
When you partner with an IT organization, you will have access to its team’s expertise in planning, executing, and analysing the results, so you will be confident you are not missing anything.
By addressing your company’s security vulnerabilities before they are exploited by cybercriminals, your business operations will be more efficient, your customers will have a better customer experience, and your profitability will increase.
If you are seeking a cyber security company in Malaysia, Cybernage not only specializes in increasing cyber resilience, assessing infrastructure, and evaluating assets, but we can also facilitate rapid business transformation through our cybersecurity services.
For more information about Cybernage, please do not hesitate to contact us.




No Comments